Staying Anonymous
Privacy is becoming more and more important in our modern world. We’re constantly tracked and having our movements sold to advertisers.
Even more so our privacy becomes a necessity if we find ourselves doing things that could get us arrested (or even killed), such as being a journalist or a whistleblower.
I am lucky enough to not suffer from such necessity, but wherever possible I do like to have control over my web browsing and other online habits.
What follows are some tools that I use to try and limit my exposure to the internet. This isn’t a ‘how to be 100% anonymous’ guide, but maybe some of these tools will be of interest to you.
I’ve broken them down into sections…
DNS
When you make a request for an online resource (for example this web page), your computer had to first convert the domain integralist.co.uk into an IP so that it could lookup the resource.
I’ve discussed how DNS works previously so I wont dive into the details of it here, but suffice to say the whole process of resolving the domain name to an IP address is something that happens unencrypted.
That means every resource you try to access will be known by your ISP, and anyone else for that matter who are snooping on the packets crossing over the network.
Additionally, a ‘man-in-the-middle’ (MITM) could modify DNS responses in such a way as to direct you to the wrong location (e.g. phishing).
To avoid these concerns you should utilize an encrypted connection to a DNS resolver. There are organizations, such as Cloudflare and Google, who offer this for free (that in itself is usually something to pay attention to for those who are very security minded).
There are currently two forms that this type of encryption can take:
- DNS over TLS (DoT)
- DNS over HTTPS (DoH)
Note: there are arguments over which is better, see this article for a breakdown of what it all means.
Here are some useful links to Cloudflare and Google if you’re interested in their services:
- Cloudflare:
- Google:
VPN
VPN stands for “virtual private network”, and is used to encrypt your internet traffic. This means no one, not even your ISP can see what resources you are requesting. All your ISP will see is you make a request to a VPN and from there you have established a secure ’tunnel’ to pass data back-and-forth.
It’s important to ensure your chosen VPN doesn’t leak DNS requests, which can occur if your VPN doesn’t offer a feature such as a ‘network kill switch’ (or ’network lock’). Typically this is handled by the VPN software you download and run on your computer.
Note: there are online tools available that help you verify your VPN isn’t leaking data.
Using a VPN also means your IP is protected and can’t be identified because resources that are requested are actually requested from the VPN server(s). IP protection can also be increased if you utilize a request pattern such as Double Hop or an extra service such as Tor.
Typically you pay for a VPN, although in some cases you might find one that offers a free tier (e.g. Windscribe). Although in the case of Windscribe that requires them to monitor your logs in order to distinguish between free tier users who are abusing their service.
Note: there are online resources for comparing different VPNs, which can be useful for helping you choose who to use.
Tracking bandwidth might be a concern to you if you’re overly security-minded, or it might be an acceptable trade-off for utilizing a free service. I personally believe that you get what you pay for, and a VPN is usually money well spent.
Paying for a VPN doesn’t have to be expensive though. I pay £6 a month which is acceptable considering I encrypt all my traffic, but I can appreciate that this might still be too much money for some people depending on circumstance.
You can find VPNs for as cheap as £1 a month (e.g. Windscribe’s custom built plans) or from as low as £2.99 with NordVPN depending on the length of the plan you select.
Tor
Tor (aka. The Onion Router) is a free service that directs your requested resource through multiple servers (much like the layers of an onion). The servers are chosen at random and increase your privacy by obfuscating the origin of the request through the use of encryption.
Tor does not replace a VPN. Tor only anonymizes your web browsing, whereas a VPN encrypts all internet traffic (e.g. locally running desktop applications, to terminal command line applications etc).
Using Tor with a VPN is possible but only really for those who require complete privacy (arguably not possible without a lot of effort).
For most typical users who want to protect their privacy and online behaviours, the additional overhead of using Tor is unnecessary when they already use a VPN.
If you feel using Tor would be a good thing, then it’s best to first connect to your VPN before opening up Tor because it means your VPN won’t be able to see what you’re doing inside the Tor network (which might be useful in the unlikely scenario where your VPN is compromised).
Equally, if there is a bug in Tor (this has happened), then the VPN will offer that extra layer of protection.
Note: there is even an entire OS that is bootable from a USB stick that routes all traffic through Tor, called Tails (see this simple rundown for a recent update, and this older review for a more general feature run through).
Web Browser Extensions
I personally use the Firefox as it offers me the best of performance and customization. Along with using a VPN I like to utilize some additional ’extensions’ (or add-ons as they’re referred to by Firefox) to extend the behaviour of my web browser and to help reduce my ability to be tracked.
The below image shows some of the add-ons I utilize:
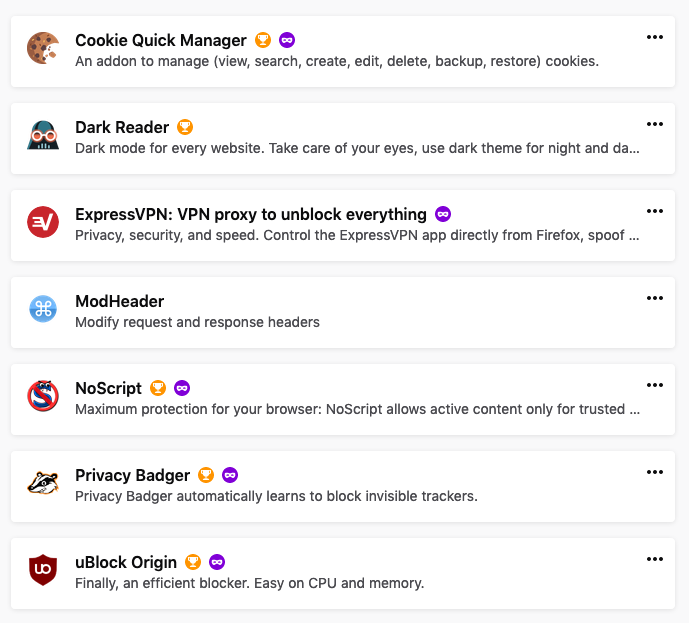
The ones of relevance here are:
- Cookie Quick Manager: simple UI for editing/deleting cookies (useful to see what’s being set and by whom!).
- Privacy Badger: blocks invisible third-party trackers.
- ExpressVPN: allows for doing things like ‘double hops’, spoofing my location, blocking WebRTC and enforcing HTTPS.
- NoScript: blocks JavaScript and allows me to configure how specific scripts are run and for how long they’re trusted.
- uBlock: blocks ads, pop ups, and trackers.
Old add-ons I used to have installed…
- Cookie AutoDelete: highly configurable way to delete cookies once you’ve finished browsing (whether it be changing domain, or tabs or browser restart).
- DuckDuckGo Privacy Essentials: blocks hidden trackers, forces encryption via HTTPS, private search data, tools for grading websites based on their privacy performance.
In the case of ‘DuckDuckGo Privacy Essentials’ I removed that once I had ‘ExpressVPN’ and ‘Privacy Badger’ installed as I needed ‘ExpressVPN’ any way (and that has ‘HTTPS Everywhere’ built-in like DDG did), but also ‘Privacy Badger’ was much a more advanced tracker blocker than DDG was.
In the case of ‘Cookie AutoDelete’ I removed that once I installed ‘Privacy Badger’ and ‘NoScript’ as both those add-ons aided with the same problem.
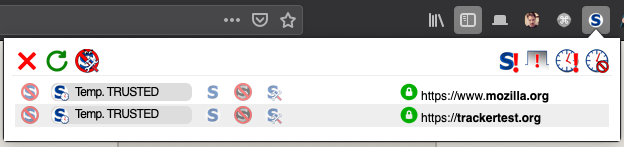
Below is a screenshot of what the ‘NoScript’ add-on looks like:
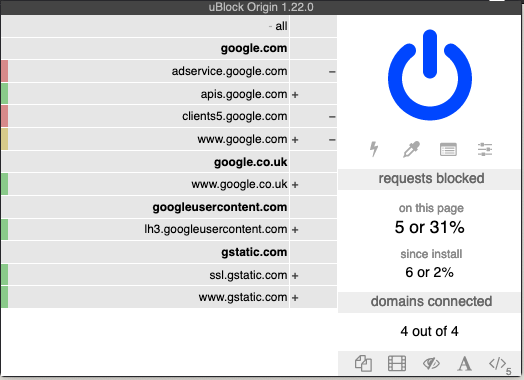
Below is a screenshot of what the ‘uBlock’ add-on looks like when visiting google.com:
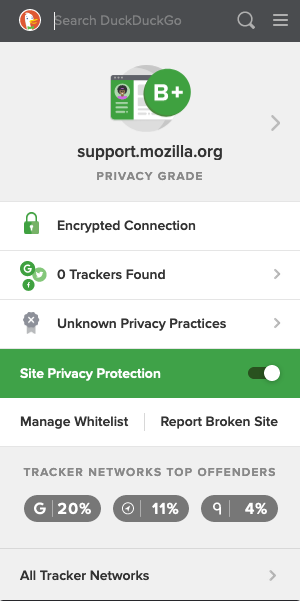
Below is a screenshot of what the ‘DuckDuckGo Privacy Essentials’ add-on looks like:
Also, each release of Firefox improves the Privacy settings available and so things like content blocking and preventing ‘browser fingerprinting’ is starting to be rolled out more generally for Firefox users:
Below is a screenshot of Firefox’s built-in “Do Not Track” setting (which is definitely worth enabling, even if respecting it is only voluntary):
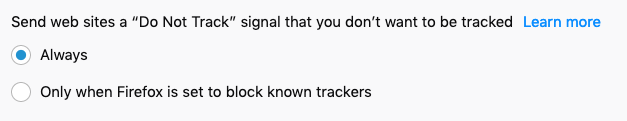
Below is a screenshot of what Firefox looks like when inspecting a web page that has had content blocked:
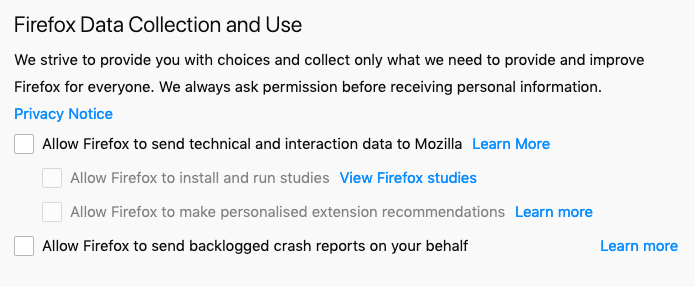
But all that said, it’s still worth checking what your browser is doing. For example, Firefox enables specific types of data collection which may be worth you disabling:
Email through free providers such as Google’s Gmail are definitely NOT private. Google has already admitted to reading their user’s emails in order to serve them advertising based on the content of their email.
If you are not paying for the service then you’re not a ‘customer’. You are in fact a ’target’.
An alternative is to use an email provider that encrypts your messages and doesn’t have access to their content in any way. A good option (which has a free tier, but obviously you’ll use up that free tier pretty quickly) is Proton.
Note: due to how they encrypt your data, if you forget your password and try to reset it, you’ll lose all your email because they don’t have a means to decrypt those files unless you provide the relevant password.
Conclusion
Remember, staying ‘anonymous’ and ‘protecting your privacy’ are actually different things. The tools I use above will not help to keep my internet actions anonymous. If you want a good breakdown of what that would take (which is a lot of effort!) then read this article by Windscribe VPN.
Security is hard, and a never ending challenge to get right. But hopefully this post has given you some ideas about the various tools you can use to help you stay anonymous and to protect your privacy.
But before we wrap up... time (once again) for some self-promotion 🙊