Key Architecture
Introduction
Just a quick post to cover the key architecture I’m using currently. I’m very interested to know how others are doing things in the hope that I can improve the security of my setup.
Note: I’m not a security paranoia nut, so I’m not looking for the most concrete solution. But definitely want to be sure I’m not missing anything obvious either
Visual
Here is a high-level view of what I have currently:
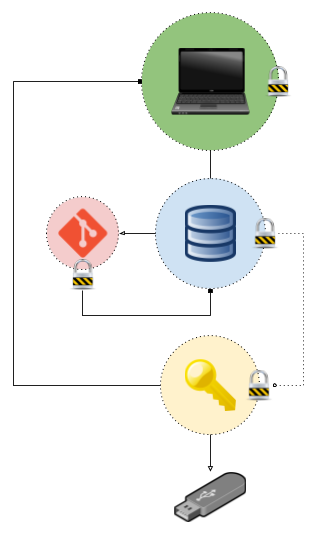
Breakdown
Let’s start at the top…
Laptop
The laptop is password protected and the hard drive is automatically encrypted
Password Data Store
The laptop contains a password data store consisting of GPG keys for every record in the data store.
In order to access the data store (or any of its records), you need a private GPG key.
The data store is backed up to a private online git repository.
Private GPG Key
The private key is itself protected by a secure passphrase (i.e. one that is almost impossible to crack - by today’s standards and recommendations - and I’ve not written it down but memorised it entirely).
The private/public key pair is stored on the laptop, but as the key is protected by a secure passphrase I feel (without going over the top on security) this is as good as I’m probably going to get with it.
The private key is also backed up onto a remote USB drive in case I lose my laptop and I need the key in order to access the data in the password data store.
Private Git Repository
The private git repo has two routes of access. The account itself with the relevant service provider and an SSH key that exists on my laptop to allow it to gain access to the contents of the repository (but not the contents of the files in the data store itself as they are protected by my private GPG key).
The passphrase for both the account and the SSH key are secure (by today’s standards and recommendations) and are stored inside the password data store.
If my laptop was lost, then I’d need to rely on the service provider’s ability to reset my account password via email, where by I could then remove the existing SSH key and replace it with a new one.
I mention replacing the SSH key because I don’t back it up. I feel this SSH key doesn’t need to be a long lasting key (unlike my private GPG key which I intend to keep as safe as possible + the offline backup as a fallback).
Vulnerabilities?
There are a few layers to this architecture and so I’m hoping this makes it harder for a compromise to be effective.
If someone compromises my laptop (i.e. gets access to it), then they can’t access the password data store as they can’t access my private key.
Although a compromise could result in a key logger being installed and record what I type for my passphrase
The only way to get my private key is to locate my remotely stored and safe USB that homes the raw private key contents.
If someone compromises the private git repository, they again can’t do anything with the contents without my private GPG key.
Note: when exporting a private key from GPG, it is by default encrypted with its passphrase (it’s not the raw key)
Conclusion
So what do you think? Is this good, bad or just plain terrible?
Please let me know your thoughts on twitter (@integralist)
But before we wrap up... time (once again) for some self-promotion 🙊